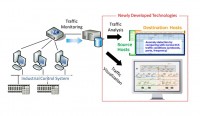
 Yokogawa Electric Corporation (Yokogawa, President: Takashi Nishijima) announces that it has worked with the National Institute of Information and Communications Technology of Japan (NICT, President: Dr. Masao Sakauchi), Professor Yasuo Okabe of Kyoto University, and former Associate Professor Hiroki Takakura of Kyoto University to jointly develop a technology that visualizes and analyzes control system traffic to verify its integrity. This technology, which has been integrated by Yokogawa in an industry-first network healthiness check service, can quickly detect security incidents such as a malware infection. This combines visualization technology with the collection and analysis of traffic data to verify the integrity of control system networks, and is expected to improve the security of control systems used in public utilities.
Yokogawa Electric Corporation (Yokogawa, President: Takashi Nishijima) announces that it has worked with the National Institute of Information and Communications Technology of Japan (NICT, President: Dr. Masao Sakauchi), Professor Yasuo Okabe of Kyoto University, and former Associate Professor Hiroki Takakura of Kyoto University to jointly develop a technology that visualizes and analyzes control system traffic to verify its integrity. This technology, which has been integrated by Yokogawa in an industry-first network healthiness check service, can quickly detect security incidents such as a malware infection. This combines visualization technology with the collection and analysis of traffic data to verify the integrity of control system networks, and is expected to improve the security of control systems used in public utilities.
Control system security has become a serious concern in recent years due to the proliferation of cyber-attacks targeting critically important infrastructure like public utilities: electric power, gas, and water. As control systems increasingly rely on operating systems and standard protocols that are both open and versatile, cyber attacks are very common now with various infection routes not only via the Internet but also via USB memory devices and other media, making it difficult to prevent all malware infections. Therefore, there is an urgent need for a technology that can quickly detect security incidents. Such technology should not have an impact on control system availability (stable, continuous operation) as these systems need to keep operating without interruption for very long periods, even as long as several decades.
NICT, Yokogawa, and Kyoto University jointly developed a technology for visualizing and analyzing control system traffic to verify its integrity and quickly detect security incidents such as malware infections.
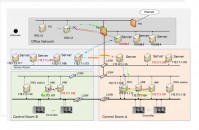
Unlike general information systems where the amount and direction of traffic keep changing, it is easier with control system networks to identify when traffic conditions are normal as these systems are designed and used for a specific purpose. We focused on this characteristic. Our technology saves data on normal control system traffic conditions as a white list. With reference to this list, the technology monitors the dynamic state of the control system network to detect any abnormalities such as an increase in traffic or communication with an unknown IP address that could be caused by malware.
Furthermore, by using NIRVANA*, a real-time traffic visualization system developed by NICT, we improved this technology to comply with unique communications protocols used by control systems. As a result, this technology can identify traffic conditions much easier when an abnormality is identified (Figures 2 and 3).
Since there is no need to install detection software on each control system host (or server), this technology is easy to be introduced and does not impact control system availability.
Dioni Tabbers
 exida invites you to attend a complimentary training on the exSILentia® Safety Lifecycle tool. Attendees will learn how to perform Safety Integrity Level (SIL) Selection and Verification using the advanced capabilities of exSILentia® . This will help users determine the required risk reduction for each hazard scenario and the achieved risk reduction for each identified Safety Instrumented Function (SIF). The class will also cover interfacing with Process Hazard Analysis (PHA) results, documentation of the Safety Requirements Specification (SRS), and operational aspects such as proof testing.
exida invites you to attend a complimentary training on the exSILentia® Safety Lifecycle tool. Attendees will learn how to perform Safety Integrity Level (SIL) Selection and Verification using the advanced capabilities of exSILentia® . This will help users determine the required risk reduction for each hazard scenario and the achieved risk reduction for each identified Safety Instrumented Function (SIF). The class will also cover interfacing with Process Hazard Analysis (PHA) results, documentation of the Safety Requirements Specification (SRS), and operational aspects such as proof testing.
 Honeywell and Palo Alto Networks® are collaborating to boost the cyber security capabilities of control systems used by industrial facilities and critical infrastructure. Honeywell's Industrial Cyber Security business is now offering the Palo Alto Networks Next-Generation Security Platform to industrial customers. The collaboration enables customers to better prevent cyber attacks against their Process Control Networks (PCN) and Operational Technology (OT) environments in order to protect their assets and maximize production uptime and safety.
Honeywell and Palo Alto Networks® are collaborating to boost the cyber security capabilities of control systems used by industrial facilities and critical infrastructure. Honeywell's Industrial Cyber Security business is now offering the Palo Alto Networks Next-Generation Security Platform to industrial customers. The collaboration enables customers to better prevent cyber attacks against their Process Control Networks (PCN) and Operational Technology (OT) environments in order to protect their assets and maximize production uptime and safety. wa Electric Corporation announces that Yokogawa Solution Service Corporation, a subsidiary that is responsible for Yokogawa's control business in Japan, has taken an order from Asahi Kasei Chemicals Corp. to provide a network healthiness check service that analyzes and verifies the integrity of the data traffic on the control system communications busses at its Mizushima Works. An industry first*, this cyber security service for control systems combines network visualization technology with the collection and analysis of data traffic.
wa Electric Corporation announces that Yokogawa Solution Service Corporation, a subsidiary that is responsible for Yokogawa's control business in Japan, has taken an order from Asahi Kasei Chemicals Corp. to provide a network healthiness check service that analyzes and verifies the integrity of the data traffic on the control system communications busses at its Mizushima Works. An industry first*, this cyber security service for control systems combines network visualization technology with the collection and analysis of data traffic. This white paper describes the distinction between failure rate prediction and estimation methods in general and then gives an overview of the procedures used to obtain dangerous failure rates for certain mechanical equipment using exida FMEDA predictions and OREDA estimations. exida frequently compares field failure rate data from various sources to FMEDA results in order to validate the FMEDA component library. However, because OREDA and FMEDA methods are quite different, it is not possible to compare their results directly. A methodology is presented which creates predictions and estimations that are more comparable. The methodology is then applied to specific equipment combinations and the results are compared. When differences in the results exist between the two methods, plausible explanations for the differences are provided.
This white paper describes the distinction between failure rate prediction and estimation methods in general and then gives an overview of the procedures used to obtain dangerous failure rates for certain mechanical equipment using exida FMEDA predictions and OREDA estimations. exida frequently compares field failure rate data from various sources to FMEDA results in order to validate the FMEDA component library. However, because OREDA and FMEDA methods are quite different, it is not possible to compare their results directly. A methodology is presented which creates predictions and estimations that are more comparable. The methodology is then applied to specific equipment combinations and the results are compared. When differences in the results exist between the two methods, plausible explanations for the differences are provided. Yokogawa Electric Corporation (Yokogawa, President: Takashi Nishijima) announces that it has worked with the National Institute of Information and Communications Technology of Japan (NICT, President: Dr. Masao Sakauchi), Professor Yasuo Okabe of Kyoto University, and former Associate Professor Hiroki Takakura of Kyoto University to jointly develop a technology that visualizes and analyzes control system traffic to verify its integrity. This technology, which has been integrated by Yokogawa in an industry-first network healthiness check service, can quickly detect security incidents such as a malware infection. This combines visualization technology with the collection and analysis of traffic data to verify the integrity of control system networks, and is expected to improve the security of control systems used in public utilities.
Yokogawa Electric Corporation (Yokogawa, President: Takashi Nishijima) announces that it has worked with the National Institute of Information and Communications Technology of Japan (NICT, President: Dr. Masao Sakauchi), Professor Yasuo Okabe of Kyoto University, and former Associate Professor Hiroki Takakura of Kyoto University to jointly develop a technology that visualizes and analyzes control system traffic to verify its integrity. This technology, which has been integrated by Yokogawa in an industry-first network healthiness check service, can quickly detect security incidents such as a malware infection. This combines visualization technology with the collection and analysis of traffic data to verify the integrity of control system networks, and is expected to improve the security of control systems used in public utilities.