 To help manufacturers and plant and facility operators improve their cybersecurity defenses and better confront the growing dangers of cyberwarfare, the International Society of Automation (ISA) today announces the availability of the ISA Cybersecurity Tech Pack.
To help manufacturers and plant and facility operators improve their cybersecurity defenses and better confront the growing dangers of cyberwarfare, the International Society of Automation (ISA) today announces the availability of the ISA Cybersecurity Tech Pack.
“The ISA Cybersecurity Tech Pack is an assembly of the latest technical papers, PowerPoint presentations, technical books and InTech articles developed by some of the world’s leading experts in cybersecurity and industrial automation and control systems security,” says Susan Colwell, manager of publications development at ISA. “These materials—which can be downloaded from the ISA website—include the latest cybersecurity strategies, recommendations and tools that can immediately be applied to protect your industrial control systems and process control networks.”
As a widely recognized, world leader in cybersecurity standards development, training and educational resources, ISA provides the proven technical expertise and know-how to help safeguard industrial automation and control systems.
For instance, the ANSI/ISA99 (IEC 62443), Industrial Automation and Control Systems Security standards—developed by a cross-section of international cybersecurity subject-matter experts from industry, government and academia—represent a comprehensive approach to cybersecurity in all industry sectors. ISA and its sister organization, the Automation Federation, is currently assisting the Obama administration and US federal agency officials develop the initial version of a national cybersecurity framework—as called for by President Obama in February of this year.
The ISA Cybersecurity Tech Pack also includes two cybersecurity-focused ISA books: the popular Industrial Network Security by David J. Teumim; and the recently introduced Industrial Automation and Control Systems Security Principles by Ronald L. Krutz, Ph.D. As an added bonus, the compilation includes many highly relevant and informative cybersecurity articles published in InTech magazine, ISA’s bi-monthly magazine for automation and control professionals.
Below is a complete list of what is included in the ISA Cybersecurity Tech Pack.
Technical papers
Cyber Security Implications of SIS Integration with Control Networks
Practical Nuclear Cyber Security
Establishing an Effective Plant Cybersecurity Program
LOGIIC Benchmarking Process Control Security Standards
Stronger than Firewalls: Strong Cyber-Security Protects the Safety of Industrial Sites
Integrated Perimeter and Critical Infrastructure Protection with Persistent Awareness
Applying ISA/IEC 62443 to Control Systems
Establishing an Effective Plant Cybersecurity Program
Getting Data from a Control System to the Masses While Maintaining Cybersecurity–The Case for “Data Diodes”
Reconciling Compliance and Operation with Real Cyber Security in Nuclear Power Plants
Wastewater Plant Process Protection—Process Hazard Analysis
Water/Wastewater Plant Process Protection: A different approach to SCADA cyber security
Using Cyber Security Evaluation Tool (CSET) for a Wastewater Treatment Plant
Improving Water and Wastewater SCADA Cyber Security
An Overview of ISA-99 & Cyber Security for the Water or Wastewater Specialist
To learn more about or purchase the Cybersecurity Tech Pack, visit www.isa.org/PR13/CYBETechPack
Nike Tiempo Legend
 exida has released a new white paper entitled: Comparing FMEDA Predicted Failure Rates to OREDA - Estimated Failure Rates for Sensor and Valve Assemblies.
exida has released a new white paper entitled: Comparing FMEDA Predicted Failure Rates to OREDA - Estimated Failure Rates for Sensor and Valve Assemblies.
 The implementation of an automatic dosing of the flocculants allows the customer to respect (24h a day, 365 days a year) the limit for phosphate in the outlet and save a lot of money: resulting in less chemicals and sludge production.
The implementation of an automatic dosing of the flocculants allows the customer to respect (24h a day, 365 days a year) the limit for phosphate in the outlet and save a lot of money: resulting in less chemicals and sludge production.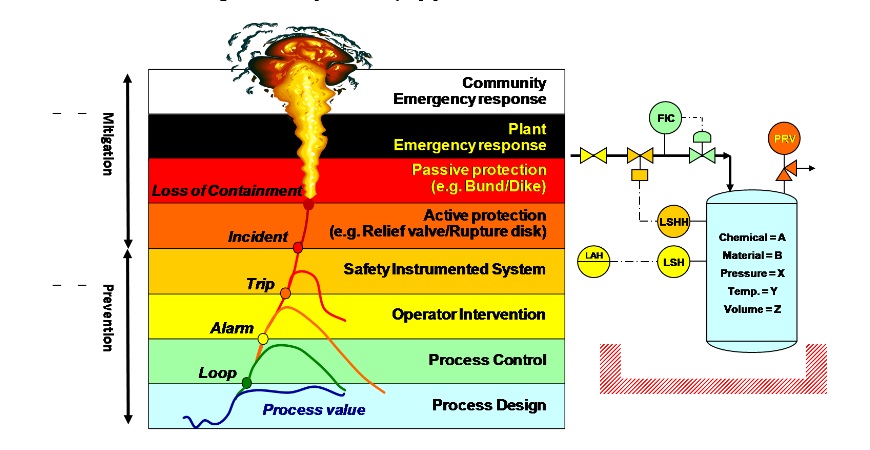 White Paper by Exida: Some of the significant process industries incidents occurred by overflowing vessels, including BP Texas City and Buncefield. In many overflow incidents, alarms were designed to signal the need for operator intervention. These alarms may have been identified as safeguards or layers of protection, but they did not succeed in preventing the incident. This paper reviews several overflow incidents to consider the alarm management and human factors elements of the failures.
White Paper by Exida: Some of the significant process industries incidents occurred by overflowing vessels, including BP Texas City and Buncefield. In many overflow incidents, alarms were designed to signal the need for operator intervention. These alarms may have been identified as safeguards or layers of protection, but they did not succeed in preventing the incident. This paper reviews several overflow incidents to consider the alarm management and human factors elements of the failures.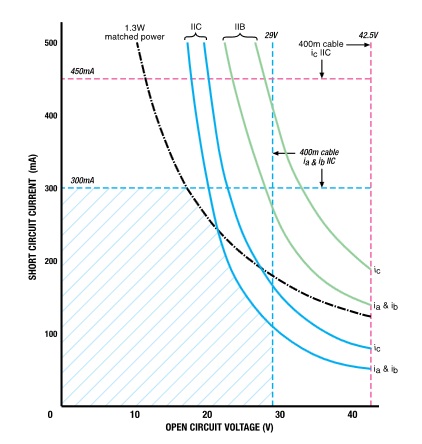 Intrinsic Safety is the natural choice for all low voltage instrumentation problems. This application note looks at the design, installation, maintenance and repair of Intrinsically Safe equipment and also considers the risks associated with dust.
Intrinsic Safety is the natural choice for all low voltage instrumentation problems. This application note looks at the design, installation, maintenance and repair of Intrinsically Safe equipment and also considers the risks associated with dust. To help manufacturers and plant and facility operators improve their cybersecurity defenses and better confront the growing dangers of cyberwarfare, the International Society of Automation (ISA) today announces the availability of the ISA Cybersecurity Tech Pack.
To help manufacturers and plant and facility operators improve their cybersecurity defenses and better confront the growing dangers of cyberwarfare, the International Society of Automation (ISA) today announces the availability of the ISA Cybersecurity Tech Pack.